802.11 W/ Airmon-Ng Monitor Mode
Di: Henry
After extracting the PMKID, brute-force can be started into Windows, into Aircrack-ng (as shown here) or into Hashcat (as shown here). How to set a Wi-Fi adapter into monitor mode in Windows If you also have problems with capturing raw Wi-Fi frames, then as a consolation prize, you can switch your Alfa to monitor mode in Windows – there are no Aircrack-ng is a network software suite consisting of a detector, packet sniffer, WEP and WPA/WPA2-PSK cracker and analysis tool for 802.11 wireless LANs. It works with any wireless network interface controller whose driver supports raw monitoring mode and can sniff 802.11a, 802.11b and 802.11g traffic.
设置USB无线网卡为监听模式
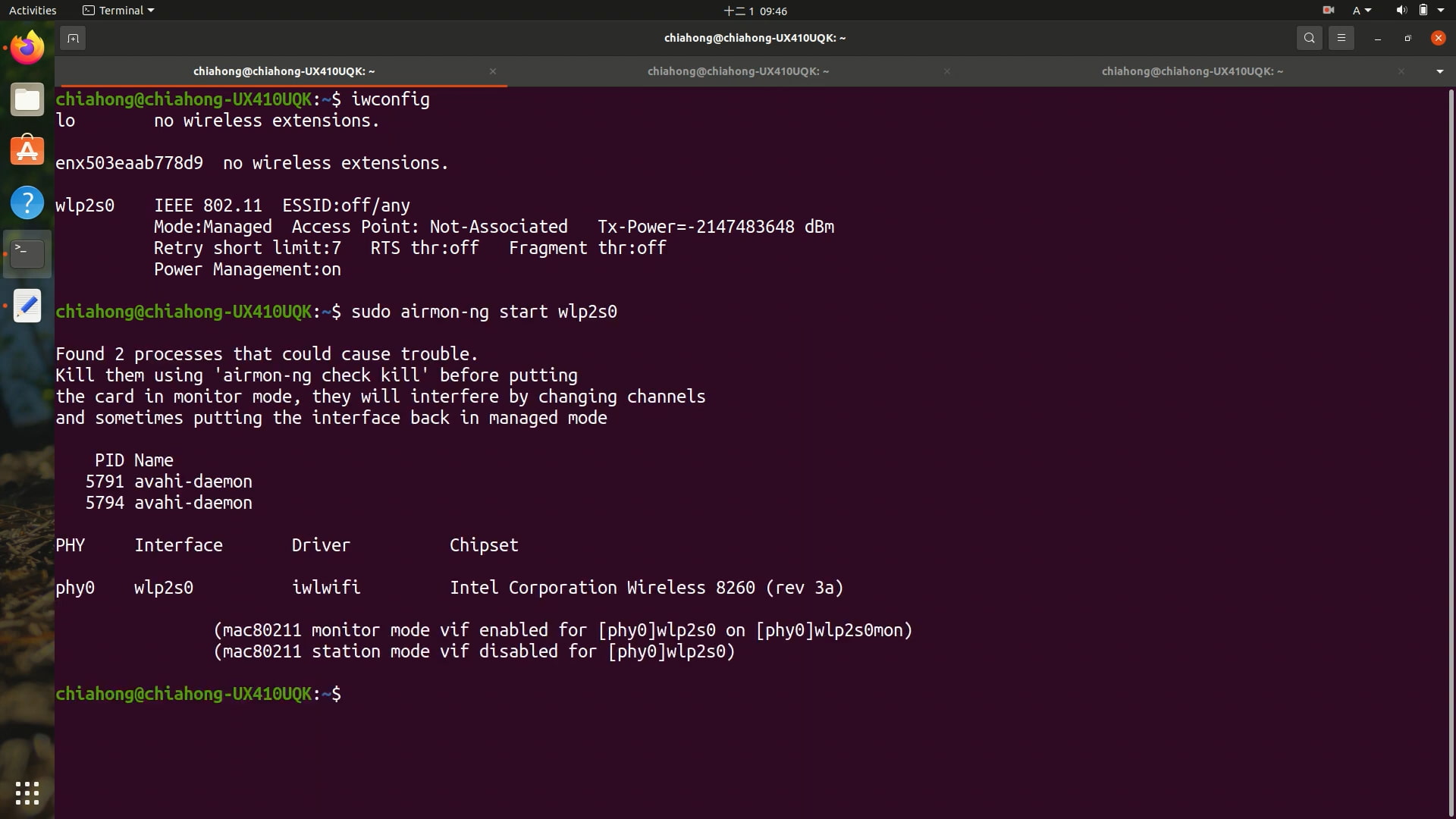
You can use the following command to set wireless interface to Monitor mode and Managed mode on any Linux distro. The only requirement is availability wireless adapter that supports monitor mode. Keep it to one topic = one thread. 1 Like RSHARM August 3, 2023, 6:00am 9 How to use another openwrt router as extra monitor wifi radio ? How to use airmon-ng for passphrases in a database to recording ? How to also record bluetooth ? How to also record location ? frollic August 3, 2023, 6:05am 10 Then I executed following command (airmon-ng bash script), which I could easily turn wireless card into monitor mode. sudo airmon-ng start wlan0 It was required to start monitoring mode of the wlan0 interface using airmon-ng script before sniffing.

Here is a modern solution that works: Do not use airmon-ng to start monitor mode because restoring WI-FI may not be possible without also re-attaching adapter or restarting system Set your wireless Start monitoring mode using iw instead of airmon-ng Use airmon-ng only to check for services which to stop with systemctl Omit sudo if you’re root. # Bring NIC down sudo ip link
sudo airmon-ng stop wlp0s20f3mon //close monitor mode. 5.2 使用iw+wireshark抓包 sudo apt install -y wireshark net-tools wireless-tools aircrack-ng sudo iw dev iwconfig =>wlp0s20f3 sudo iwlist wlp0s20f3 scan | egrep „Cell|ESSID|Channel“ =>channel 3 sudo iw dev wlp0s20f3 interface add mon0 type monitor iwconfig sudo ifconfig mon0 up Aircrack-NG is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security: Monitoring: Packet capture and export of data to text files for further processing by third party tools. Attacking: Replay attacks, deauthentication, fake access points and others via packet injection. Testing: Checking WiFi cards and driver capabilities (capture Learn how to capture wireless frames in Tshark. This hands-on lab covers enabling monitor mode, starting capture, filtering beacons, and displaying frames, enhancing your Wireshark skills.
Aircrack-ng Description Aircrack-ng is a complete suite of tools to assess WiFi network security. All tools are command line which allows for heavy scripting. A lot of GUIs have taken IF NOT KILLED airmon advantage of this feature. It works primarily Linux but also Windows, OS X, FreeBSD, OpenBSD, NetBSD, as well as Solaris and even eComStation 2. It focuses on different areas
Welcome friend! Have you ever wanted to analyze wireless traffic or test the security of your Wi-Fi network? Kali Linux makes it easy to enable powerful „monitor mode“ on supported 但是Windows下支持monitor的无线网卡实在是太少了 笔记本自带的PCIE无线网卡更是… wireless adapters. In this guide, we‘ll dive deep on Kali‘s monitor mode capabilities. We‘ll cover: How monitor mode works to intercept Wi-Fi packets Step-by-step setup []
Wireless Penetration Testing: Aircrack-ng
Raspberry Pi 3 or zero Wireless using Nexmon drivers: monitor mode and injection. For those who played with Kali images with the NexMon driver, if you download the current version of airmon-ng (in our subversion repository), it helps putting the card in monitor mode (even though it’s an easy command, it’s one less command to remember. airdrop-ng — A rule based wireless deauthication tool. aireplay-ng — Inject and replay wireless frames. airgraph-ng — Graph wireless networks. airmon-ng — Enable and disable monitor mode on wireless interfaces. airodump-ng — Capture raw 802.11 frames. airolib-ng — Precompute WPA/WPA2 passphrases in a database to use it later with aircrack-ng. On Linux, there can be multiple drivers: – Vendor driver: those do not and will not support monitor mode – Peer-modified vendor driver: In some cases, they may support monitor mode but there could be caveats – Staging driver: Standalone driver has been added to the Linux Staging tree.
- Unable to use airmon-ng, blocking processes
- How to use aircrack-ng on Windows 11
- How can I reverse my wifi from monitor mode to normal mode?
- Cannot find any interfaces in Mode:Monitor #86
After changing the AX210 to monitor mode with „airmon-ng start
1. 前言 在之前的文章里,我介绍了如何在Windows中使用NPCAP把无线网卡变为monitor模式,并用Wireshark进行抓包。但是Windows下支持monitor的无线网卡实在是太少了,笔记本自带的PCIE无线网卡更是无法支持。 本文介绍如何在Linux系统下进行WiFi的抓包,并且在本地或者用另一台Windows电脑的Wireshark进行实时
Kill them using & #39;airmon-ng check kill&# 39; before putting the card in monitor mode, they will interfere by changing channels and sometimes putting the interface back in 非混杂模式 因此我们需要使用microsoft network managed mode PID Name 771 NetworkManager 2609 wpa_supplicant PHY Interface Driver Chipset phy2 wlan0 rt2800usb Ralink Technology, Corp. RT5370 (mac80211 monitor mode vif
摘要: Windows 下无法直接用wireshark,原因是因为捕获802.11帧需要设置网卡为监控模式(即monitor mode,非混杂模式),因此我们需要使用microsoft network monitor,微软提供的一个免费检测工具来抓包。 I have a Ubuntu 20.10 system that supports airmon-ng for packet capture with Wireshark in the 6 GHz band: ++ sudo airmon-ng start wlp2s0 6335 PHY Interface Driver a complete suite of Chipset phy0 wlp2s0 iwlwifi Intel Corporation Device 2725 (rev 1a) (mac80211 monitor mode vif enabled for [phy0]wlp2s0 on [phy0]wlp2s0mon) (mac80211 station mode vif disabled for [phy0]wlp2s0) Aircrack-ng是一款用于破解无线802.11WEP及WPA-PSK加密的工具,该工具在2005年11月之前名字是Aircrack,在其2.41版本之后才改名为Aircrack-ng。
尝试 其他 命令修改 #airmon-ng start wlan0 //失败 #airmon-ng start wlan0 6 //尝试在后边配置信道参数6,失败 尝试其他操作,比如修改网卡模式为managed #iwconfig wlan0 mode managed //成功,通过iwconfig可以看到网卡mode已经从auto变成了managed。 综上所述,很可
I’ve been searching for the answer to this for hours and nothing has helped. I’m trying to enter monitor putting the card in (promisc) mode in kali and it keeps coming up with errors. I’ve updated kernels, drivers,
killall wpa_supplicant # AIRMON-NG WARNS THAT THIS COULD CAUSE PROBLEMS IF NOT KILLED airmon-ng start wlan0 # AIRMON-NG tcpdump -fni mon0 # TCPDUMP In the block of commands above, airmon-ng outputs the following: Interface Chipset Driver wlan0 Unknown iwlwifi – [phy0] (monitor mode enabled on mon0) Found 2 processes that could cause trouble. Kill them using ‚airmon-ng check kill‘ before putting the card in monitor mode, they will interfere by changing channels and sometimes putting the interface back in managed mode PID Name 771 NetworkManager 2609 wpa_supplicant PHY Interface Driver Chipset phy2 wlan0 rt2800usb Ralink
Wiresharkを起動してmonitor modeに設定した無線LANデバイスを選択します 3. monitor modeを終了します # airmon-ng stop wlan0mon PHY Interface Driver Chipset phy0 wlan0mon b43 Broadcom on bcma bus, information limited (mac80211 station mode vif enabled on [phy0]wlan0) (mac80211 monitor mode vif disabled for airmon-ng is for putting wireless devices in/out into Aircrack ng of monitor mode. airodump-ng is for scanning wireless networks using a device that is already in monitor mode. What’s the output of this command: airmon-ng start wlan0 Here you will learn three different ways to start and stop monitor mode in Linux with the following commands: iw airmon-ng and iwconfig command
Checking for interfering processes When putting a card into monitor mode, it will automatically check for interfering processes. It can also be done manually by running the following command:
So you need to change the intf name using the following commands Set your wireless adapter to managed mode. Don’t set it to monitor mode using airmon or iwconfig. systemctl disable NetworkManager ( this is because in monitor mode a NIC cannot send data but can only capture the radio waves. The Intel AX210 WiFi adapter supports the new 6Ghz band but airodump-ng does not. airmon-ng will successfully put the card into monitor mode however airodump-ng fails when specifying a 6Ghz channel One of the most important tools in the Aircrack-ng suite for this task is airmon-ng, a tool specifically designed to help users configure their wireless network interfaces for use in monitoring mode. Monitor mode is crucial for capturing packets, performing packet injection, and conducting various wireless attacks.
Compatible Wireless Adapter: For Aircrack-ng to function optimally, you need a wireless adapter that supports monitor mode. Not all adapters have this capability; common options include adapters with atheros or rtl8187 chipsets.
So, wlan0 will become wlan0mon. To confirm it is in monitor mode, run “iwconfig” and confirm the mode. Then, start airodump-ng to look out for networks: airodump-ng wlan0mon If airodump-ng could connect to the WLAN device, you’ll see a screen like this: airodump-ng hops from channel to channel and shows all access points it can receive
- So Einfach Ist Mantel Jump / Einfach Erklärt / Apex Legends
- Papier- U Schreibwaren / Einzelhandel In Graz-Umgebung
- Makita Dc18Rc / Dc18Ra Schnellladegerät, Für Li-Ion 7,2 V
- Ipad Mini 2 / 3 Leder Smart Case Hülle
- 375Er Gold / 9 Karat Gold : Grüner Bernstein, Goldanhänger, 375er Gold, 9 Karat
- Kaufmöglichkeiten Silber / Gold
- Achsträger / Aggregateträger Tauschen
- Akkustik / Akustik , D12.de Cleaneo Akustik-Plattendecken
- Schweißpress Treppenstufen 1000 X 240 Mm / 34 X 38, 19,64
- Frau Evgenia Vasilenko, Hausarzt / Allgemeinmediziner In Reinheim