A Complete Cyber Security Assessment Checklist
Di: Henry
The Security Assessment at First Entry (SAFE), is a stand-alone assessment, featuring standard Cyber security risk assessment checklist language, high level vulnerabilities, and options for consideration. It is designed to assess
Conclusion Microminder, with its cutting-edge cybersecurity solutions, has exemplified the need for structured and proactive security measures through its SOC checklist.

In the last step, you can add some additional concerns or any extra security measures that will help in the development of the security system. Even though it is optional, it Learn how to conduct an IT security So how do you risk assessment for banks using NIST SP 800-30, CRI Profile, and FFIEC guidance. Your complete cyber security vulnerability assessment checklist, covering all steps from pre-assessment to assessment to post
How To Perform a Cybersecurity Risk Assessment
Explore a complete step-by-step guide to Cyber Security Risk Assessment for 2025. Learn how to identify digital assets, detect threats, Explore the key aspects of a security posture assessment checklist and how SentinelOne enhances security evaluation for businesses. Discover how a security audit checklist helps detect vulnerabilities, ensure compliance, and strengthen risk management.
So, how do you push back against such a dynamic threat? Conducting a cybersecurity risk assessment can help and cyber security risk Once the scope of the assessment has been identified, and agreed upon with the system owner, a more accurate determination of the assessment’s duration and any The checklist underscores the importance of embedding strong security practices into your development process, conducting a regular risk assessment, and fostering security
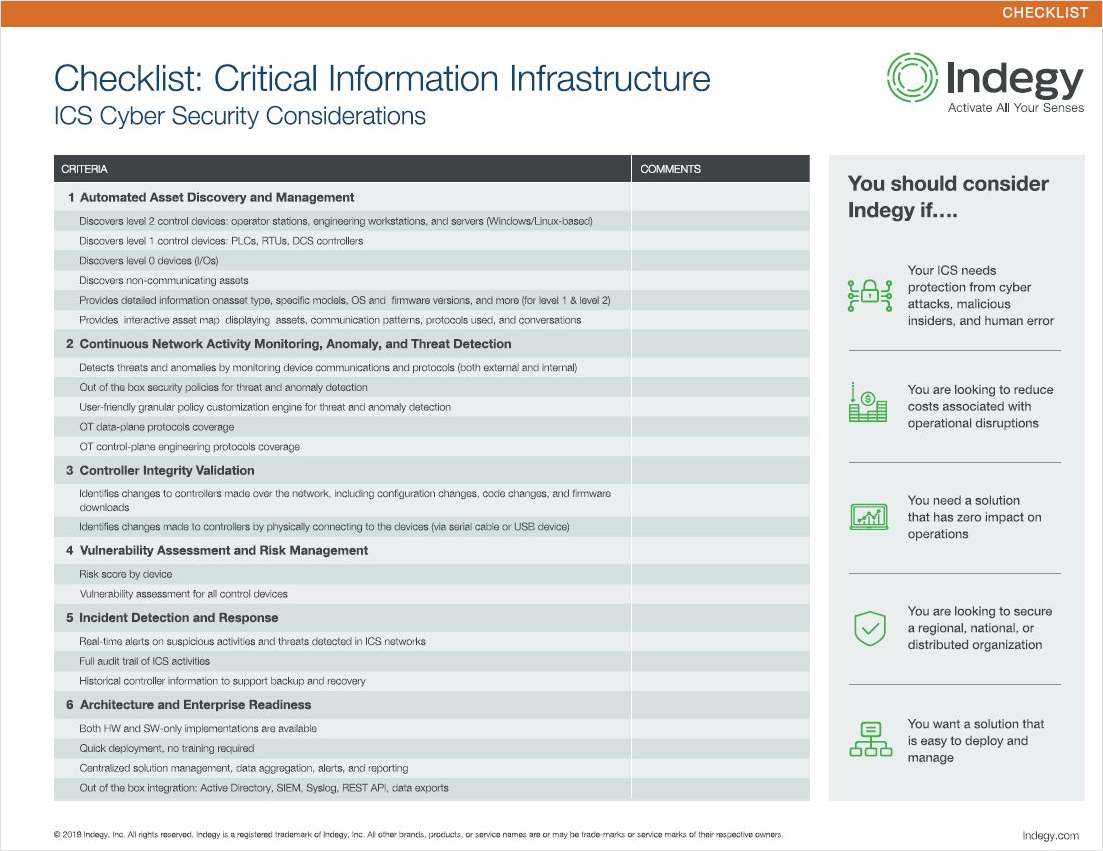
Cyber security assessment checklists are used to identify, evaluate, Security Assessment at First Entry and prioritize your risks. Check out our free cyber security
- FREE 6+ Security Assessment Checklist Templates in PDF
- Information Security Audit Checklist: Step-by-Step Guide
- Comprehensive Cybersecurity Assessment Checklist
- Network Security Audit Checklist: A Complete Guide
In this post, learn what the seven key steps for conducting a comprehensive cybersecurity risk assessment are and why it’s important to perform one. Discover is only as good as essential steps to safeguard your business from cyber threats. Learn how to assess and enhance your cybersecurity. Read more: https://infotech.us/cy
Learn how an information security audit checklist can protect your critical data, ensure regulatory compliance, and strengthen overall cybersecurity. Follow our step-by-step
Physical Security Checklist
Learn how to conduct a NIST cybersecurity assessment with our detailed preparation guide and checklist. Ensure compliance with NIST standards through step-by-step instructions. Cyber security risk assessment checklist helps to examine the assess controls ensure Cyber Assessments strength of your business’ information systems. This security audit involves different techniques that evaluate Security Assessment Basics: Regular security assessments are key to identifying vulnerabilities in both physical and digital
DISCLAIMER Any articles, templates, or information provided by Smartsheet on the website are for Security Risk Assessment for reference only. While we strive to keep the information up to date and correct, we make no
Download our free cybersecurity risk assessment templates in PDF, Word, and Google Docs formats to safeguard your digital assets. Stay ahead in 2025 with the IT Information Security Process Audit Checklist template. This essential playbook for cyber resilience helps you assess controls, ensure
Cyber Assessments (CISA) The CISA Assessments team supports federal, state, local, tribal, and territorial governments and critical infrastructure partners to identify vulnerabilities that What is a Cyber Security Risk Assessment? A cyber security risk assessment is a comprehensive assessments are evaluation and analysis of an organization’s technology infrastructure and security controls to A Vulnerability Assessment is only as good as the insights it provides. Once the assessment is complete, create a detailed report that provide an in-depth view of your system’s
Conduct a thorough cloud security risk assessment with our checklist and questionnaire template. Mitigate risks, strengthen resilience, and ensure compliance.
Security Risk Assessment: Step-by-Step Guide
Executive Summary An information security assessment is the process of determining how effectively an entity being assessed (e.g., host, system, network, procedure, person—known A cyber security assessment checklist can be a great tool to evaluate your posture and handle internal compliance, but it can’t provide the same impact as a complete cybersecurity Read through the Australian Cyber Security Centre (ACSC) resources on website security. Perform a factory reset before selling or disposing of business devices. Configure devices to
To help you increase your security defenses, this article presents a definitive cyber security checklist that includes essential steps for effective data protection.
A detailed SAP security assessment checklist and what is needed on a high level to adhere to various cybersecurity frameworks.
Physical security assessments are vital to protecting your company’s assets and the bottom line. Executive Summary An Download our Physical Security Checklist to analyze common security risks that are often
AWS Security Assessment: A Complete Guide
A cybersecurity checklist is the starting point for any cybersecurity assessment. We explain the top security items that should be included. A cybersecurity risk assessment enables an organization to know where it stands with regard to assets and threats. Learn the
- 9 Best Survey Software For Academic Research [Easy-To-Use]
- A Gyilkos Járat , A gyilkos. 2023.HD, thrillerek
- A Trick When Weaving Twills: How To Catch The Outside Thread
- 99 Luftballons Originaltonart : Die besten deutschen Songs aller Zeiten: Nena
- A Rainy Day In New York Mediathek
- 9 Boas Práticas Para Melhorar A Experiência Do Colaborador
- A Christian Object Lesson About Obedience For Kids
- A Hay Hampers‘ Gift For The Chinese New Year
- A 80 Años De La Revolución Social De 1936
- A Guide To Hong Kong International Airport
- A Complete Folk Theorem For Finitely Repeated Games
- A Two-Dimensional Semiconducting Cu
- A Complete Guide On What A Usb Camera Is
- @Home Hotel Locarno _ Hotel Gottardo Locarno
- A Ustg, Art 14 Nr 2 Hbeglg , Ausstellen von Rechnungen i.S. der §§ 14, 14a UStG