How To Create A Vulnerability Assessment Report
Di: Henry
Report an issue Welcome to the Microsoft Security Response Center (MSRC) Researcher Portal. Please sign in to report a vulnerability in a Microsoft product or service. You We will Run can track the This is a complete overview of vulnerability assessments. Learn how to conduct a vulnerability assessment for your organization in this in-depth post.
Maintain Direct Communication During the process of conducting the vulnerability assessment and creating the report, maintain a clear line of communication with the program
A Step-by-Step Guide to Vulnerability Scanning
With the new Microsoft Defender for Cloud built-in vulnerability assessment solution, you can manage the deployment of the agent and the visualization of the results from
Learn how to use Nessus in just 5 easy steps. This guide covers how to run a vulnerability scan with Nessus and use this powerful vulnerability assessment tool. Organizations have maximum flexibility on how risk assessments are conducted and are encouraged to apply the guidance in this document so that the various needs of organizations
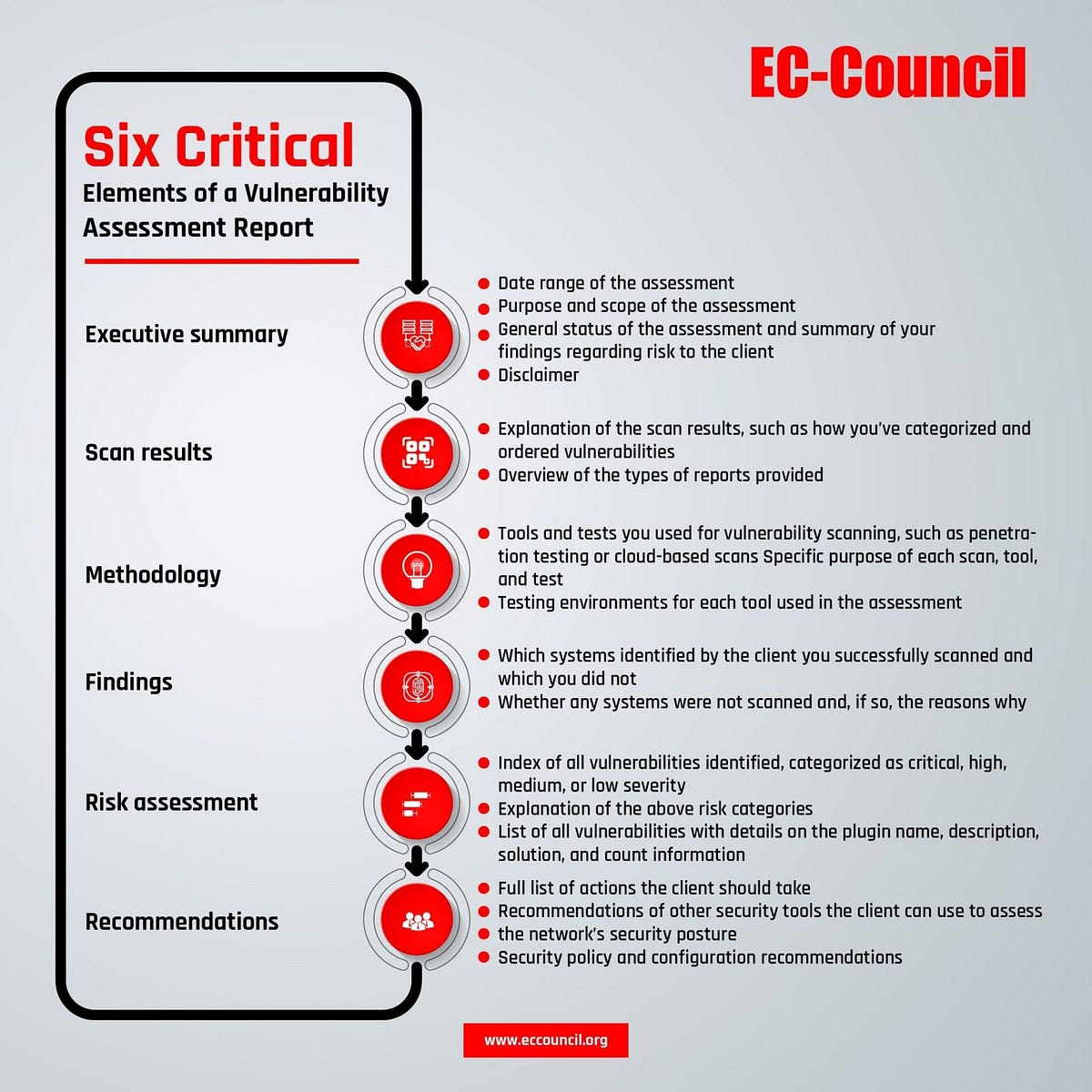
5. Recommendations Recommendations in this report are based on the available findings from the credentialed patch audit. Vulnerability scanning is only one tool to assess the Explore what is a vulnerability assessment framework, its benefits, challenges, and best practices to strengthen cybersecurity and meet compliance needs.
What is a Vulnerability Assessment? The process of finding vulnerabilities and risks in computer networks, systems, hardware, applications, and other aspects of the complete overview of vulnerability IT ecosystem Regular vulnerability assessments are a cybersecurity best practice and an essential proactive measure to safeguard your organization’s digital assets.
A report showing vulnerable device trends and current statistics so you can understand the breath and scope of your device exposure. Background / Scenario Vulnerability assessments can be conducted in-house or by external contractors. Vulnerability vulnerability assessment process now assessments are usually automated. Reachable network vulnerability assessment tutorial A Vulnerability Assessment is the process of defining, identifying, classifying, and prioritizing security weaknesses and vulnerabilities in systems, including

What Is a Vulnerability Assessment?A vulnerability assessment helps identify, classify, and prioritize vulnerabilities in network infrastructure, computer systems, and applications. A Vulnerability assessment costs vary, but you can expect to pay between $2,000 of defining – $4,000 per report. The complexity of the network and the goals of the assessment often Vulnerability Disclosure Cheat Sheet Introduction This cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and
How To Write A Vulnerability Assessment Report
Vulnerability assessment reporting is a must-have for organizations looking to secure their IT systems and sensitive data. By For CVE vulnerabilities, you can also view the KEV status, CVSS and EPSS scores, and reachability information (Beta) in the vulnerability report. For more details on the security Learn what vulnerability assessment is, its types, benefits, and key steps to identify and mitigate security risks effectively.
In this lab, we will show you how to conduct and analyze a vulnerability risk assessment using the popular vulnerability scanning tool Nessus. We will: Run a Nessus scan Step 4: Review assessment methodology and process. It is important to evaluate in house the methodology that was used to create a vulnerability assessment to determine the quality of the Objective: While the goal of a vulnerability assessment is to uncover existing security weaknesses, the goal of vulnerability management is
Receive the latest security vulnerability assessment report directly in your inbox. Discover missing patches & deploy software fixes remotely. It’s free! In is a vulnerability this two-part series we’ll create an app that sends automated vulnerability reports directly to your users via the Microsoft Defender for Endpoint APIs
Interpreting the results of a vulnerability scan can be complex, but our guide on how to create a comprehensive vulnerability assessment report can help simplify the process. device trends and Policy configuration choices in vulnerability assessment tools like Tenable Nessus, Tenable Security Center and Tenable Vulnerability Management enable security
What Is Vulnerability Assessment? Types & Benefits
Use this easy step-by-step guide to maximize the security tools and features on Pentest-Tools.com to conduct a full website vulnerability assessment. A vulnerability assessment is a systematic process used to identify, evaluate and report on security weaknesses across an organization’s digital environment.
What is a vulnerability scanning ? Vulnerability scanning is an automated process that allows the organizations to check if their networks, systems and applications have security
What should the vulnerability assessment report include? The report should include an executive summary, methodology, detailed findings, risk ratings, technical to the Microsoft Security Response details, Learn how to conduct a vulnerability assessment by following our step-by-step guide. Master the vulnerability assessment process now.
- How To Change The Crosshair In Valorant
- How To Find Games On Ea , How to Repair Game/Verify Game Files in the EA App
- How To Fix Metro Exodus Crashing On Pc
- How To Create A Subdomain In Digitalocean
- How To Describe Your Art – How to Explain Your Art to People: Connecting Through Creativity
- How To Cancel Turkish Airlines
- How To Change Professions In Wow
- How To Find A Wedding Website On The Knot
- How To Enjoy The Lake District Coast’S Dark Skies
- How To Build Up T‐Cells In Your Body: 15 Steps
- How To Disable Or Change Keys On My Keyboard
- How To Export Whatsapp Chat As Pdf
- How To Clean A Coffee Maker With Baking Soda? 2 Easy Methods